The mantra of every corporation should be, "Don't collect what you can't protect."
It should matter not if you are the CEO of very large corporation or organization like Target, Home Depot, Anthem Blue Cross Blue Shield, Costco or a tiny entity like your general practice MD, if you are collecting data on your customers, patients, members, etc, you must protect the information.
There exists three common themes and only one of these is because the individual user is practicing poor cyber hygiene.
- My company or customer data has no value
This begs the question then why do you keep customer lists? But if you do, make sure you share in your company privacy statement exactly how you are going to collect the information collected, which portions of the information are retained and which portions are shared.
I'll get to security of my company or customer data when I have - time, funds, or am compelledReally? The year is 2015, we must put the security and privacy of our customers and employees first. WIth the average cost of a data breach at greater than $150 per record, a breach of a mom & pop entity could effectively put the small business out of business. The larger organizations and corporations have no excuse, they can afford and should invest in security and privacy controls over the data collected. The smaller entities and sole proprietorships truly are constrained by cash-flow and operational expenses. This cash crunch often times means only doing what is compelled by regulatory compliance and which is not synonymous with putting in place as secure an infrastructure as possible with that same amount of funds.
My customers made their own account vulnerableYes individuals (all of us) follow the path of least resistance and it is difficult to manage passwords, given 90 percent of our online engagements require us to log in to engage. People will reuse their passwords, and this is where things go sideways. The alleged iCloud compromises were not caused by a defective system, they were caused by the "celebrities" reusing their password and email combinations and not utilizing the two-step authentication processes available. What can a company do to help themselves? Require strong passwords for your users (remind them during the password creation step to not reuse a previously used password); implement two-step authentication, so in the event a customer reuses the password/email combination they have another level of authenticating protection to someone trying to access their account. In this manner, you are promoting and projecting good cyber hygiene practices upon your customer/clients.
------------
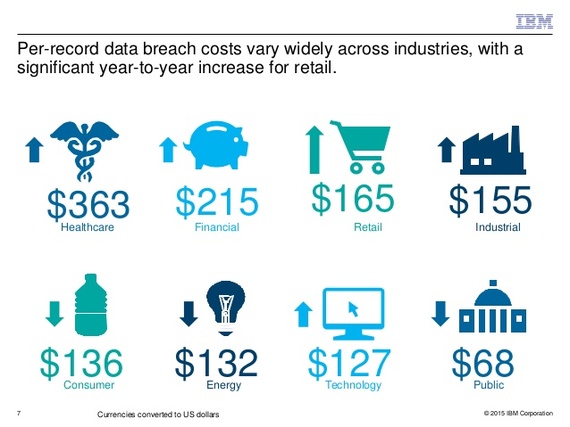
IBM reports, in their publically available presentation on the cost of a data breach, that while the average is $153 per record, in healthcare it is a whopping $363 per record.
------------
What every company should do is sit down and convene the equivalent of an all-hands and do a comprehensive survey on what information is being collected, how is it being used, how is it being protected, when is it exposed to the risk of compromise and when is it in its most protected state. Following this self-examination, then start putting together mitigation tasks which start with, "How can we be totally compromised by an insider, what customer or employee data have we lost" and work back down to the point of contact with customers/clients.
Know what your worst case scenarios are, before they are the scenarios about which you must respond. There is great value in exercising the mantra "Don't collect, what you can't protect."
Support HuffPost
Our 2024 Coverage Needs You
Your Loyalty Means The World To Us
At HuffPost, we believe that everyone needs high-quality journalism, but we understand that not everyone can afford to pay for expensive news subscriptions. That is why we are committed to providing deeply reported, carefully fact-checked news that is freely accessible to everyone.
Whether you come to HuffPost for updates on the 2024 presidential race, hard-hitting investigations into critical issues facing our country today, or trending stories that make you laugh, we appreciate you. The truth is, news costs money to produce, and we are proud that we have never put our stories behind an expensive paywall.
Would you join us to help keep our stories free for all? Your contribution of as little as $2 will go a long way.
Can't afford to donate? Support HuffPost by creating a free account and log in while you read.
As Americans head to the polls in 2024, the very future of our country is at stake. At HuffPost, we believe that a free press is critical to creating well-informed voters. That's why our journalism is free for everyone, even though other newsrooms retreat behind expensive paywalls.
Our journalists will continue to cover the twists and turns during this historic presidential election. With your help, we'll bring you hard-hitting investigations, well-researched analysis and timely takes you can't find elsewhere. Reporting in this current political climate is a responsibility we do not take lightly, and we thank you for your support.
Contribute as little as $2 to keep our news free for all.
Can't afford to donate? Support HuffPost by creating a free account and log in while you read.
Dear HuffPost Reader
Thank you for your past contribution to HuffPost. We are sincerely grateful for readers like you who help us ensure that we can keep our journalism free for everyone.
The stakes are high this year, and our 2024 coverage could use continued support. Would you consider becoming a regular HuffPost contributor?
Dear HuffPost Reader
Thank you for your past contribution to HuffPost. We are sincerely grateful for readers like you who help us ensure that we can keep our journalism free for everyone.
The stakes are high this year, and our 2024 coverage could use continued support. If circumstances have changed since you last contributed, we hope you’ll consider contributing to HuffPost once more.
Already contributed? Log in to hide these messages.

